In this article
Understanding NCII
Let's be honest, most of our secrets live in our phones these days, not in our heads. And with smartphones and cloud backups, your private moments can slip into the world faster than juicy gossip at a family gathering. On the other hand, social media and anonymous platforms make spreading this data a breeze.
This has contributed to the rise in Non-Consensual Intimate Imagery (NCII) cases across different countries. So, how do you keep your privacy safe in a connected world, and what is NCII?
This article will help you understand NCII and show you the tools and resources you can use if your sensitive data ever gets misused.

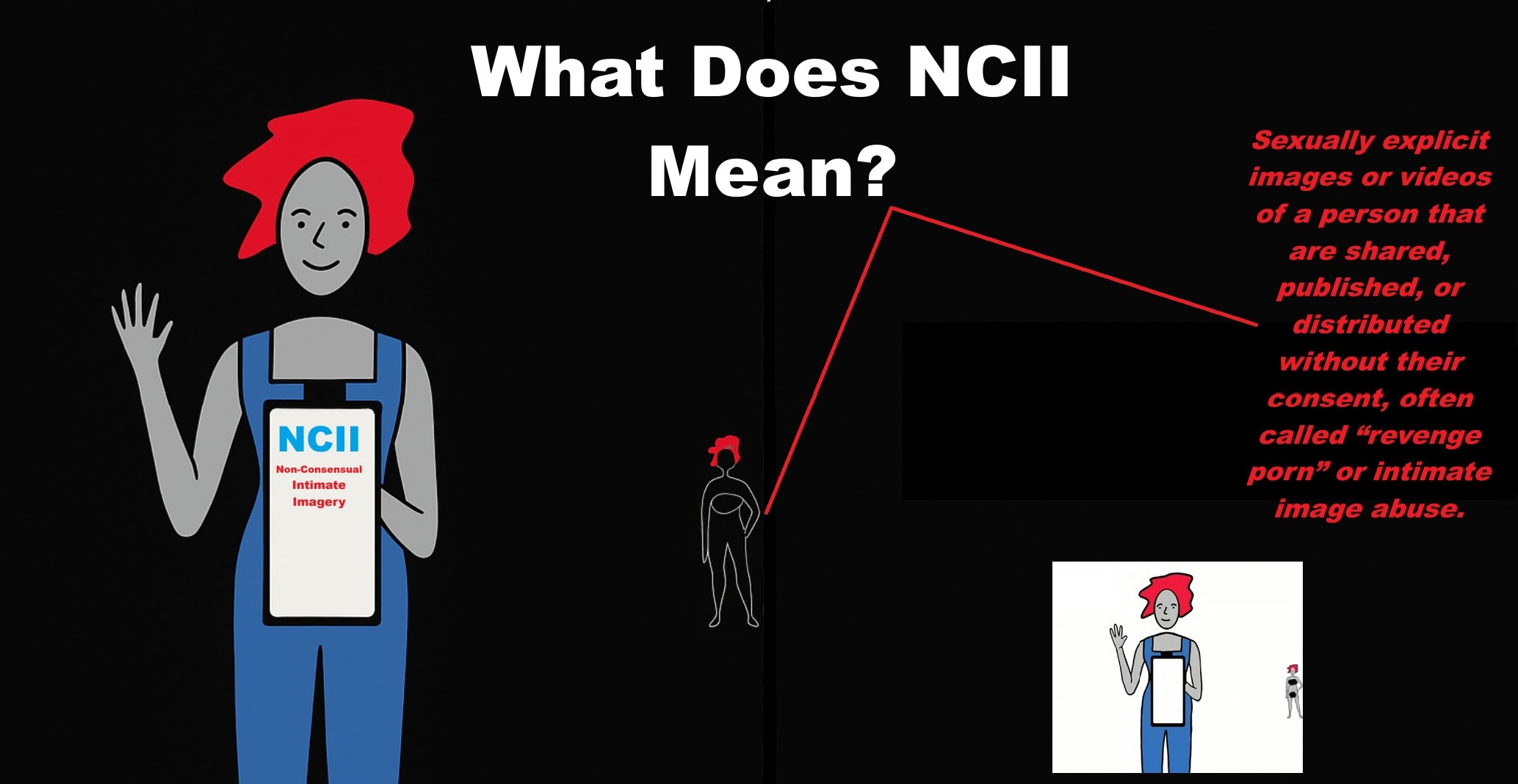
NCII, which is the abbreviation of Non-Consensual Intimate Imagery, is a form of image-based abuse. This happens when your private data gets shared without your consent. Some people call it "revenge porn," but sometimes it's more about control, bullying, or blackmail.
Data-Driven Global Analysis of NCII Abuse
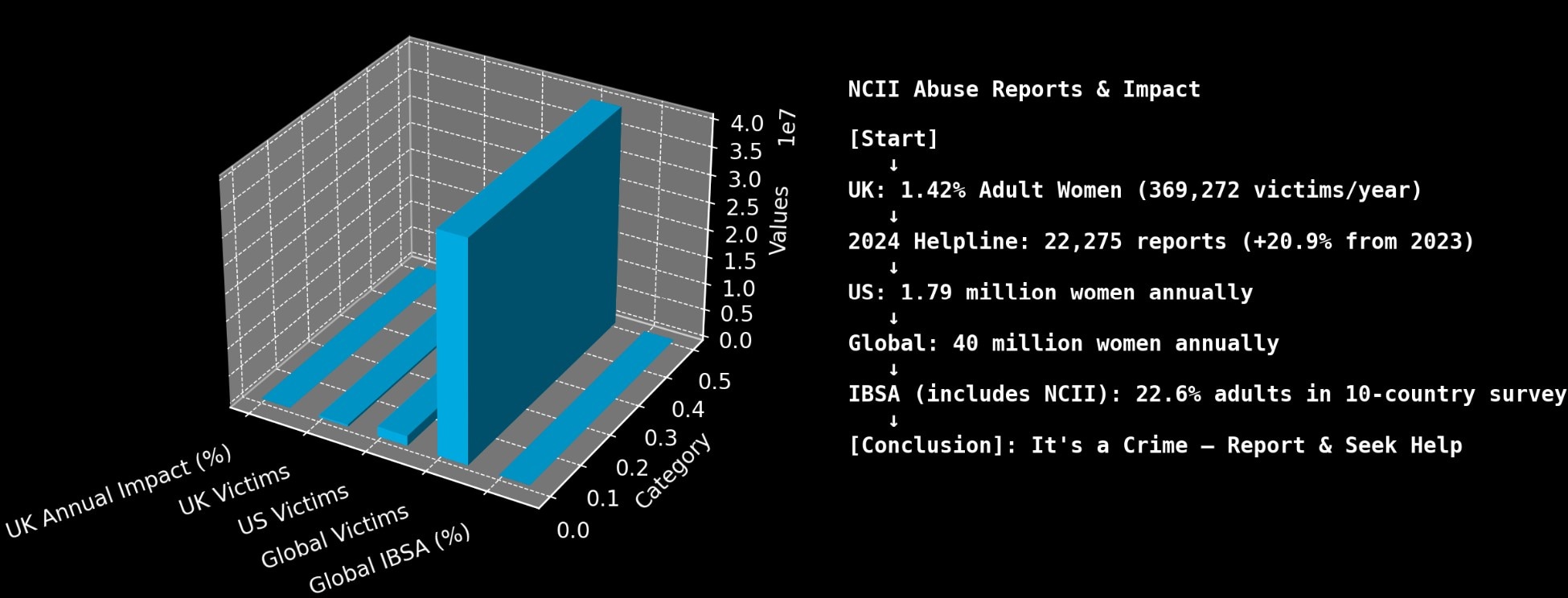
A report in the United Kingdom shows that about 1.42% of adult women experience NCII abuse annually. In the United States, an estimated 1.79 million women are affected by NCII abuse annually. Then, a survey conducted across 10 countries with over 16,000 adult respondents revealed that 22.6% had experienced image-based sexual abuse (IBSA).
However, due to the dangers and life-damaging nature of NCII abuse, it is now a crime.
Key Notes of Non-Consensual Intimate Imagery
If anyone shares your sensitive information in public without your permission, it's not just a privacy violation; it can also have serious emotional and legal consequences.
Below are the key elements of non-consensual intimate imagery.
How Some NCII Content Is Created Without Consent

"Without Consent" in this context means you did not permit the sharing of your private data. Below are how Non-Consensual Intimate Imagery (NCII) abuse can be initiated.
Common Forms of NCII Abuse

Here are different forms of NCII abuse.
Tools and Resources to Fight Non-Consensual Intimate Imagery
Even in trusted relationships, once you share, control is gone. So, awareness is your first defense against Non-Consensual Intimate Imagery. Next is reporting and demanding that the content be removed. Below are reliable tools, support networks, and strategies to help protect yourself or someone else.
Verified Platforms for NCII Content Removal
| Platform | Serves | ID Needed | Removal Time |
| StopNCII.org | Adults, minors | No | 1 to 3 days |
| Take It Down (by NCMEC) | Minors, young adults | Yes | 1 to 7 days |
| Childline x IWF Report Remove Tool | Minors | Yes | 1 to 5 days |
How Parents and Educators Can Help with Non-Consensual Intimate Imagery Control
As a parent or educator, you can help young digital users combat the challenges surrounding Non-Consensual Intimate Imagery abuse. Below are ways you can be of great assistance.
- Start open conversations
- Teach digital boundaries
- Use parental controls
- Explain that sharing intimate images without permission can cause legal risks
- Encourage reporting to you or another trusted adult for help.
How to Report Non-consensual Intimate Imagery on Social Platforms
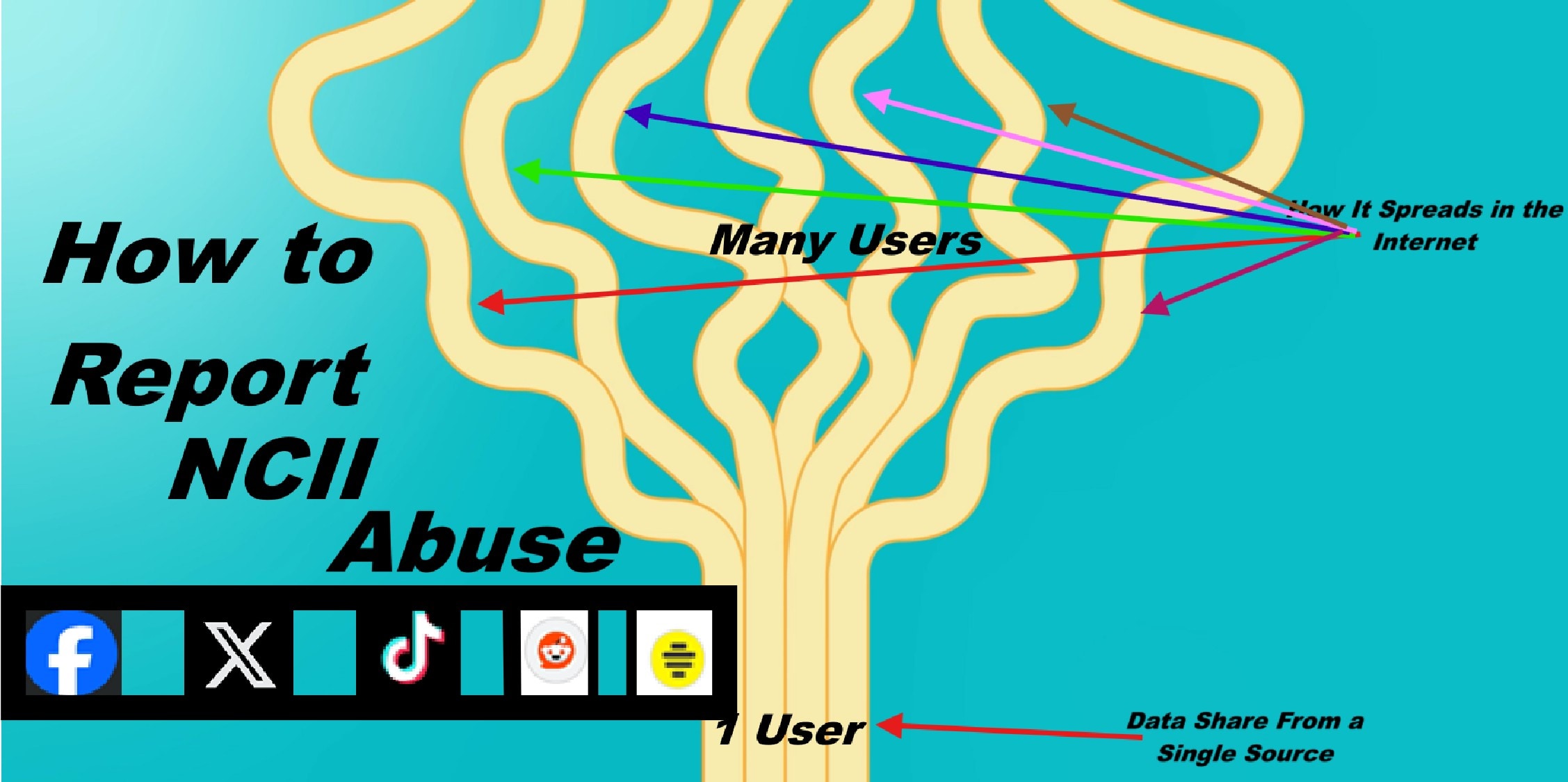
Even if you only meant to share something privately, once it's online without your permission, you lose control, and reporting becomes vital. Here's how to act quickly and effectively across major platforms.
| Platform | Reporting Steps |
| Instagram / Facebook | ● Tap the "..." menu on the post or image. ● Select "Report." ● Choose "It's inappropriate." ● Follow the prompts to flag NCII. |
| TikTok | ● Tap the share arrow on the video. ● Select "Report." ● Choose "Nudity/Sexual Content." ● Confirm the report. |
| X (Twitter) | ● Click the "..." on the post. ● Select "Report." ● Choose "Abusive or harmful." ● Select "Unauthorized photo of me." |
| ● Click "report" under post/comment ● Choose "Involuntary Pornography." ● Optionally, email contact@reddit.com with the URL. |
Meta's NCII Reporting Flow: Meta partnered with StopNCII.org to protect intimate images by using a hashing system that lets you report images without uploading them directly, keeping you in control.
How to retain anonymity when reporting
You can protect your identity while taking action. Keep things simple and safe.
- Use reporting tools within each app. They don't expose your info.
- Platforms like Meta, TikTok, and Reddit let you report anonymously.
- org only uses image hashes, not your image or identity.
- For Discord, report through the Safety Center or the Trust & Safety form. You don't share personal details.
What to Do If You're a Victim of NCII

Take the following steps to protect yourself and respond effectively:
- Document evidence. Take screenshots, note URLs, and timestamps.
- Hash the image. Use tools like StopNCII.org to create a digital fingerprint of your content.
- Report it. Follow the platform steps above swiftly.
- Seek support. Reach out to trusted friends, counselors, or legal professionals.
Legal Consequences for Non-consensual Intimate Imagery Offenders

Non-consensual Intimate Imagery abuse is treated as a criminal offense across several jurisdictions. Below are examples.
| Jurisdiction | Legal Status of NCII | Potential Penalties |
| United States | NCII is illegal in 49 states and Washington, D.C. | Penalties vary by state; they can include fines, imprisonment, and mandatory registration on sex offender lists. |
| United Kingdom | It's a criminal offense under the Criminal Justice and Courts Act 2015. | Offenders can face up to 2 years in prison and might also end up on the Violent and Sex Offender Register. |
| Australia (New South Wales) | Creation and distribution of explicit deepfakes without consent is criminalized. | Up to 3 years in prison for creation; up to 6 years for distribution. |
| Canada | Criminal offense under the Protecting Canadians from Online Crime Act (2014). | Fines and/or imprisonment; offenders may be required to register as sex offenders. |
| South Africa | Criminal offense under the Films and Publications Amendment Act (2019). | Fine up to R150,000 and/or imprisonment up to 2 years; increased penalties if the victim is identifiable. |
Global Examples:
Common Mistakes That Make NCII Harder to Combat
Don't Compromise Privacy: How to Create Privacy-Safe Videos with Filmora

Wondershare Filmora protects your private data by processing everything locally on your device. Nothing is automatically uploaded to the cloud, so your files stay in your hands until you share them. This reduces the risk of breaches and unwanted access.
On the other hand, if you want to share some intimate content online safely but do not want it used against you tomorrow, consider Filmora's face-blurring, background masking, and selective mosaic tools. These make it possible to hide faces, remove sensitive details, and keep subjects safe, without sacrificing video quality.
Creating Privacy-Safe Videos with Filmora's Secure Editing Tools
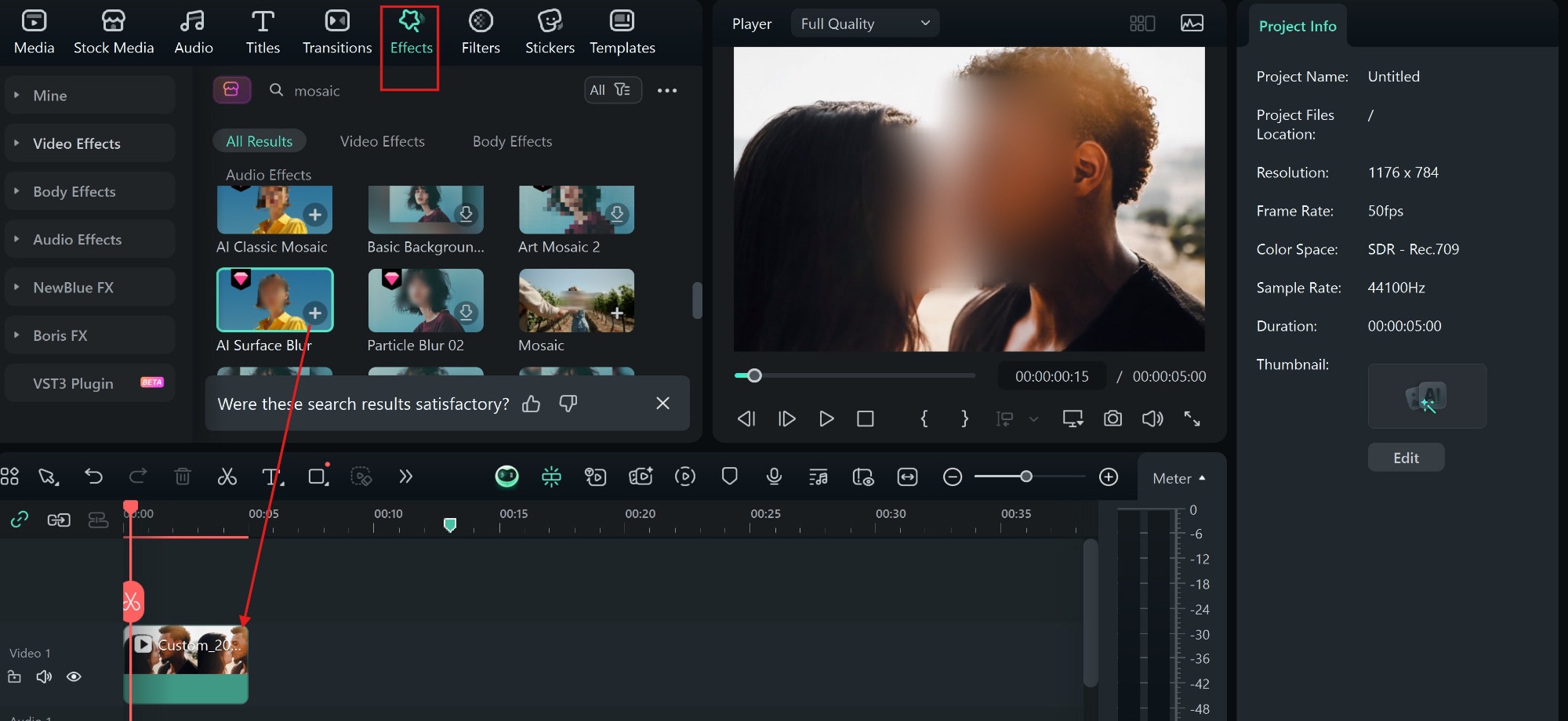

Pro Tips for Creating Safe Videos with Filmora
- Use Filmora's motion tracking with mosaic.
- Follow moving subjects in real time.
- Frame footage to avoid showing faces.
- Apply privacy filters early in editing.
- Replace risky scenes with stock footage.
Conclusion
Non-consensual Intimate Imagery (NCII) awareness videos save lives by educating and protecting communities, but privacy is key. With Filmora, you get creative freedom and strong security in one tool. Every effect, blur, and edit stays local to your device, giving you full control over sensitive content. Start creating impactful, safe awareness videos with Filmora today.